What roles exist in verifiable credentials?
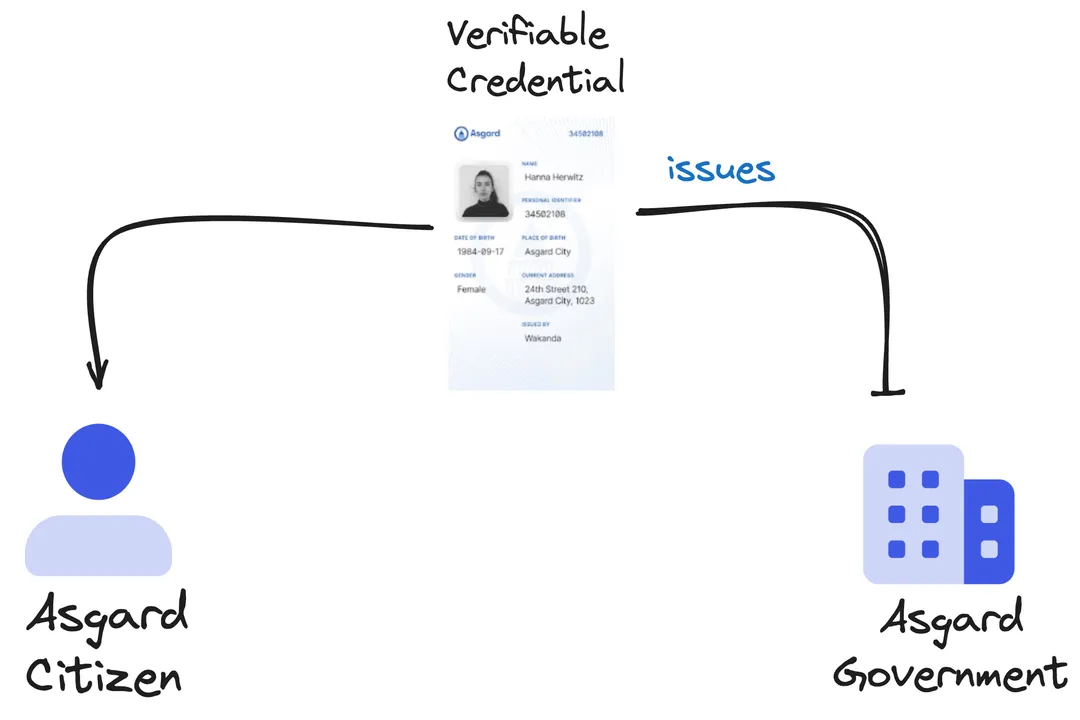
The architecture of Verifiable Credentials (VCs) relies on clearly defined interactions between distinct participants, forming a digital trust ecosystem. Understanding who does what is central to grasping how digital proof moves securely from creation to acceptance without reliance on central authorities for every transaction. This system is fundamentally structured around three main actors, though the operational reality involves necessary supporting components that sometimes blur these lines.[1][3][5]
# Primary Actors

The foundation of any VC interaction rests upon the interplay of three roles: the Issuer, the Holder, and the Verifier. These are the non-negotiable entities required for the creation, possession, and validation of a digital claim.[4][5][9]
# Issuer Functions
The Issuer is the entity that creates and cryptographically signs a Verifiable Credential, asserting that the information within it is true about the subject named in the credential.[1][3] Think of this as the digital equivalent of an accredited university issuing a diploma or a government agency issuing a driver's license. The Issuer vouches for the facts contained within the credential.[4][9]
For an Issuer, the primary responsibility is ensuring the accuracy and integrity of the data they issue. This requires maintaining secure key management systems to produce valid digital signatures, which link the Issuer's identity—often represented by a Decentralized Identifier (DID)—to the credential content.[2][7] Furthermore, an Issuer must have mechanisms in place to manage the lifecycle of the credential, which includes revoking a credential if the underlying claim becomes invalid (e.g., a professional license is suspended). [1] A key technical aspect for Issuers, as noted in discussions around the underlying data model, is defining the correct structure of the credential, including setting appropriate expiry dates and issuance timestamps.[2]
# Holder Functions
The Holder is the individual or entity that receives, stores, and controls the Verifiable Credential after it has been issued.[3][5] In a typical scenario, the Holder is the person whose identity or qualification the credential attests to. They possess the digital wallet or storage mechanism where the signed VC is kept secure.[4][6]
The Holder’s main power in this model is control over their data. They decide when, where, and to whom they will present a credential.[1] This autonomy is critical; unlike traditional paper documents, the Holder is not merely a passive recipient. They actively choose to disclose the information.[4] Advanced capabilities expected of a Holder often involve supporting selective disclosure, meaning they can present only the specific piece of information required by the Verifier (e.g., showing proof of age without revealing the exact birth date) rather than the entire document.[6] Secure storage is paramount, as possession of the credential implies ownership of the attested attribute.
# Verifier Functions
The Verifier is the entity that accepts and validates the Verifiable Credential presented by the Holder.[1][3] This actor relies on the credential to make an automated decision—perhaps granting access, confirming eligibility, or completing a background check.[4] Their interaction closes the loop of trust.
The Verifier's critical task is to confirm three things: first, that the Holder genuinely possesses the credential; second, that the Issuer actually issued it (by checking the signature against the Issuer’s public key); and third, that the credential has not been revoked. The process demands access to the Issuer’s public keys, often via a mechanism like a DID resolution service, to confirm the digital signature's validity.[7] If the signature checks out and the credential status is active, the Verifier can trust the assertion made within the credential.[5]
# Supporting Ecosystem Roles
While the Issuer, Holder, and Verifier form the essential trust triangle, the entire system cannot function securely without underlying technical infrastructure roles dedicated to identity management and resolution.[7]
# Decentralized Identity Agents
In many modern implementations, the Holder and sometimes the Issuer interact not directly, but through an Agent. This Agent acts as an intermediary or a software component within a digital wallet or an Issuer’s backend system, handling the cryptographic signing, storage, and communication protocols required for VC exchange.[6] While the Agent performs the mechanics, the underlying role of controlling the data remains with the Holder or Issuer.
# DID Method Operators
Decentralized Identifiers (DIDs) are the unique identifiers used by Issuers and sometimes Holders within the VC infrastructure to anchor their verifiable claims.[7] A DID Method defines the rules for creating, resolving, and deactivating these DIDs.[7] Operators or systems adhering to a specific DID Method (like did:ion or did:web) are essential because they establish the standardized way public keys and service endpoints—which the Verifier needs to check signatures—are published and retrieved. Without a functional DID Method, the Issuer's public identity cannot be reliably accessed for verification.[7]
# Credential Registry and Revocation Services
Although the ideal VC interaction is peer-to-peer, real-world trust often requires a check against an authoritative source for status updates. This brings up the role of a Revocation Registry or a status checker.[1] When a Verifier needs to ensure a credential is still valid, they might query a service maintained by the Issuer, often pointed to via a service endpoint listed in the Issuer’s DID document.[2] This is a specialized service role, crucial for managing the credential lifecycle after issuance, particularly for high-stakes credentials.
# Role Dynamics and Interactions
The interaction flow dictates how these roles transition between being active and passive. For instance, when a credential is created, the Issuer is active and the Holder is receiving; when presented, the Holder is active and the Verifier is receiving/processing.[3]
A core concept often overlooked is that these roles are not mutually exclusive across an organization, though they are distinct during a single transaction. For example, a university acts as an Issuer for student transcripts, but that same university might act as a Verifier when accepting a faculty member's prior degree from another institution.[4] Furthermore, an individual might be a Holder of a professional certification, yet act as an Issuer for a short-term training certificate they created for an internal team.
| Role | Primary Action | Key Output/Input | Security Focus |
|---|---|---|---|
| Issuer | Attestation and Signing | Cryptographically Signed VC | Key Management, Revocation Lists |
| Holder | Possession and Presentation | Disclosure of Verified Data | Secure Wallet Storage, Consent |
| Verifier | Acceptance and Validation | Trust Decision (Accept/Reject) | DID Resolution, Signature Verification |
| [1][5] |
Considering the security overhead for an organization moving into this space, the single biggest initial hurdle for a new Issuer is not the VC format itself, but establishing a secure, fault-tolerant system for private key protection and signing ceremonies. An inexpensive self-managed key solution suitable for low-volume, low-risk credentials might be acceptable initially, but for high-volume, high-stakes attestations (like official government IDs), the infrastructure must meet rigorous standards for key security, potentially involving Hardware Security Modules (HSMs) or specialized vault services to prevent mass compromise from a single breach.
# Trust Anchors and Identity Control
The security of the entire chain fundamentally depends on the trust anchors, which are typically the DIDs used by the Issuer and Verifier.[7] The relationship between DIDs and VCs is so intertwined that it is difficult to discuss roles without acknowledging the DID infrastructure. A DID provides the mechanism for the Verifier to find the public key needed to check the private key signature placed by the Issuer.[7] This separation of concerns—where the Issuer signs with a private key and the Verifier checks against a publicly available DID Document—is what replaces the need for a centralized certificate authority, making the system more decentralized.[7]
When assessing an external entity wishing to act as an Issuer, a practical step for any potential Verifier is to create a small checklist focused solely on the Issuer’s identity durability. This involves checking: 1) Is their DID method well-established and unlikely to become deprecated soon? 2) Does their DID Document include verifiable recovery mechanisms? 3) Do they have a publicly stated, easily accessible policy for credential revocation? Answering these questions determines the long-term viability of accepting claims from that Issuer.
This reliance on DIDs means that technical considerations are often about the resolution process—how quickly and reliably can the Verifier look up the public key associated with the Issuer’s DID?[8] In some cases, the Holder might even use a DID for their presentation, linking the proof of possession back to their own decentralized identity.[6]
# Data Model Implications for Roles
The W3C Verifiable Credential Data Model specification provides the underlying schema that formalizes what each role manages.[2] For the Issuer, the model defines the required fields for the credential envelope, such as the @context, id, type, and crucially, the issuanceDate and potential expirationDate.[2] The actual claim data resides within the credentialSubject, which identifies the person or thing the credential is about.
For the Holder, the data model implies the need for parsing capabilities. The wallet software must be able to ingest the JSON structure, verify the signature against the Issuer’s public key (found via the DID resolution), and securely store the data until requested.[2]
For the Verifier, the model specifies the structures used for presenting the credential, including the use of proofs—the cryptographic data that ties the credential to the Holder's presentation (if using selective disclosure) and confirms the Issuer's original signature.[2] The Verifier’s software must be configured to correctly interpret these proof structures to build confidence in the presentation.
Ultimately, the roles in verifiable credentials define a contract of trust, secured cryptographically and anchored by decentralized identifiers. The Issuer promises truth, the Holder controls disclosure, and the Verifier confirms authenticity based on public information.[1][4] This distribution of responsibility is what makes the resulting digital proof far more resilient and privacy-respecting than previous digital identity methods.[5]
Related Questions
#Citations
What are the key roles in Verifiable Credentials? - Sunbird RC
Verifiable Credentials Data Model v2.0 - W3C
Verifiable Credentials: A Simple Guide to How They Work
What are Verifiable Credentials and Why You Should Care About ...
Verifiable credentials - Wikipedia
Verifiable Credential support per role - iSHARE Developer Portal
Verifiable Credentials and Decentralised Identifiers - GS1 Reference
When implementing verifiable credentials, there are important ...
What are Verifiable Credentials and how do they work? - One Identity

