What roles exist in e-voting systems?
Electronic voting, or e-voting, encompasses any process that uses electronic means to assist in or handle the casting and counting of ballots. [3] The goal behind adopting this technology often centers on enhancing election efficiency, reducing costs, speeding up result tabulation, and improving accessibility for various populations, such as overseas citizens or those with mobility impairments. [4][5] However, because this technology touches the fundamental act of casting and counting votes, its implementation shifts responsibilities and creates distinct functional and human roles that are essential to maintaining integrity and public confidence. [5][7]
# Functional Components
Within any e-voting system, various functional roles must be performed, whether by dedicated hardware, software, or integrated processes. These functions span the entire voting lifecycle, from a voter making a choice to the final tally being published. [5]
One primary functional role is Vote Input and Marking. This is how the voter interacts with the system. This can range from filling in an oval on a paper ballot that is then scanned, to using a dedicated Ballot Marking Device (BMD). [2] BMDs, often required to provide accessible interfaces like audio, large text, or sip-and-puff devices, play the specific role of translating a voter's intent into a machine-readable format on a physical ballot. [2][3] In systems without paper ballots, such as older Direct Recording Electronic (DRE) systems, this role involves recording the selection directly into computer memory via a touchscreen or buttons. [2]
The second critical function is Vote Recording and Storage. This role determines where the official choice resides. In paper-based electronic systems, the human-readable paper ballot serves as the primary record, and the electronic record is secondary or used only for initial tabulation. [2][5] Conversely, DRE systems primarily record the vote in memory components, which necessitates an audit mechanism like a Voter Verified Paper Audit Trail (VVPAT) to create an independent physical record for verification, a consensus point among security experts. [2][3] Hybrid systems combine these roles, allowing a voter to mark an electronic ballot which is then printed, scanned, and tabulated. [2]
A third major role is Vote Tabulation and Consolidation. This is the role of counting the votes. Some systems, like Precinct Count Optical Scanning (PCOS), execute this at the polling place. Others use a Central Count System where precinct ballots are collected and counted centrally using high-speed scanners. [2][5] In systems using internet voting (i-voting), this function is handled by a Central Vote Server that tallies votes after the remote casting period ends. [7] Even the simple aggregation of results from various tally sheets or machines, often performed using spreadsheets, carries the functional role of final summation, though this step has historically been a source of error if not strictly controlled. [3]
Finally, the system must fulfill the role of Verification and Auditing. This is perhaps the most debated functional role, as systems lacking a paper record can only be verified indirectly through certification and security protocols. [5] Systems with paper trails allow for manual recount verification, where the paper record is the official ballot of record. [2][5] End-to-end verifiable systems aim to provide cryptographic proof that the vote was recorded as cast and tallied as recorded, independent of the underlying software. [3]
# Human Management Roles
The proper functioning of these technical roles relies heavily on the human roles involved in the system's lifecycle, from initial development through deployment and auditing. The inherent secrecy required for voting—the separation of voter identity from the ballot—makes the system fundamentally different from standard information technology, placing high importance on the roles responsible for security and oversight. [5][7]
The Electoral Management Body (EMB) or state/local election officials hold the paramount role of ultimate responsibility and ownership. [5] They must define the goals for using e-voting, manage procurement, and ensure the chosen solution fits the local context. [5] In the US, for instance, State Secretaries of State or State Boards of Elections act as the final approving authority for system use within their jurisdictions. [6][9] This role is crucial for retaining oversight and avoiding dependence on the vendors who build the technology. [5]
Vendors and Developers serve the role of system creators. They design, build, and often maintain the proprietary software and hardware. [5] Due to reliance on vendor competence and proprietary code, security experts often argue that the EMB must have access to source code to fulfill its oversight role effectively. [3][5] An interesting tension exists here: vendors are typically reluctant to provide source code access for security or commercial reasons, yet advocacy groups argue that publishing the code allows for broader scrutiny necessary for trust. [5]
Testing Laboratories and Certification Agents fill the vital quality assurance role. In the US, this is formalized by the Election Assistance Commission (EAC), which oversees accredited Voting System Test Laboratories (VSTLs). [6] These labs test systems against the Voluntary Voting System Guidelines (VVSG) to verify functionality, accessibility, and security. [6] State-level bodies, like election commissions or secretaries of state, often use these reports to issue their own certification or approval, creating a layered role of verification. [6][9] For example, in Texas, the Secretary of State conducts an examination after the federal certification process. [9]
Election Administrators and Poll Workers execute the system on Election Day. Their role is operational and procedural, requiring rigorous adherence to established steps—from checking in voters using Electronic Poll Books to verifying zero tapes at poll opening and securing materials post-closing. [1][9] The successful introduction of e-voting often requires significant capacity building and training for these roles, as the responsibility shifts from many localized poll workers to a centralized system managed by fewer, highly trained staff. [5]
Auditors and Observers play the indispensable role of independent verification. This can involve conducting mandated post-election audits, such as the partial manual counts required in some US states, or observing the testing and deployment phases. [5][9] In jurisdictions using paper records like VVPATs, auditors verify the electronic count against the physical evidence. [2][5] When systems are paperless, the audit role becomes one of confirming that the process followed prescribed, certified security procedures, which is inherently more difficult to communicate to the public. [5]
# The Voter's Evolving Role
The voter's role has transformed from simply marking a paper ballot to actively verifying an electronic process. While e-voting offers increased convenience, this convenience comes with the implied responsibility for voter verification.
The voter is expected to confirm that the electronic selections match their intent, often by reviewing a printed VVPAT slip before depositing it. [2][5] In internet voting, this verification role is more abstract, often relying on a Confirmation Code to check that the vote was received unaltered by the server, rather than viewing a physical representation of their choices. [3][5]
An important, though often overlooked, element is the Digital Literacy role required of the modern voter. While e-voting aims to bridge the digital divide for those who are remote or have disabilities, the introduction of complex systems like Ballot Marking Devices or internet voting implicitly demands a baseline level of technical familiarity. [4] If voters do not understand the technology, their ability to perform their verification role—and thus their trust in the outcome—can be compromised. [5] In environments where e-voting systems are only understood by a small cadre of experts, the public trust layer of the E-Voting Pyramid of Trust is severely weakened, regardless of technical soundness. [5] The failure to invest in civic and voter education as a core function of the implementation is a common oversight that stalls social acceptance. [5]
# Regulator Roles in Certification
Across jurisdictions, the role of the regulator is defined by what level of federal standard compliance they mandate. While the EAC's Voluntary Voting System Guidelines (VVSG) provide a baseline for federal certification, state laws dictate the mandatory role of this baseline. [6]
A comparison of state approaches reveals distinct regulatory roles:
| State Regulatory Role | Baseline HAVA Requirement | Requires Testing to Federal Standards | Requires EAC-Accredited Lab Testing |
|---|---|---|---|
| Minimal Oversight | Alaska, Hawaii, Mississippi, Montana, Nebraska, Puerto Rico [6] | Arkansas, California, Connecticut, Georgia, Kentucky, Nevada, New York, Oregon, Pennsylvania, Rhode Island, South Carolina, Tennessee, Utah, Virginia, Wyoming [6] | Arizona, Arkansas, Iowa, Maryland, Massachusetts, Minnesota, Missouri, Nevada, New Mexico, North Carolina, North Dakota, Oregon, Rhode Island, South Carolina, South Dakota, Utah, Washington, Wisconsin [6] |
| Key Action | Ensure system is legal; state/local body ultimately approves [6] | State body uses federal standards as a minimum requirement [6] | State body requires evidence from an accredited, independent third party [6] |
This matrix illustrates that a state's regulatory role can range from simply adopting baseline HAVA requirements to actively requiring third-party, federally-accredited testing before state-level approval, as seen in states like Maryland or South Carolina. [6] Furthermore, some states, like Texas, layer their own examination process on top of federal certification, establishing a unique final gatekeeper role for the Secretary of State. [9]
# Blockchain and Decentralized Roles
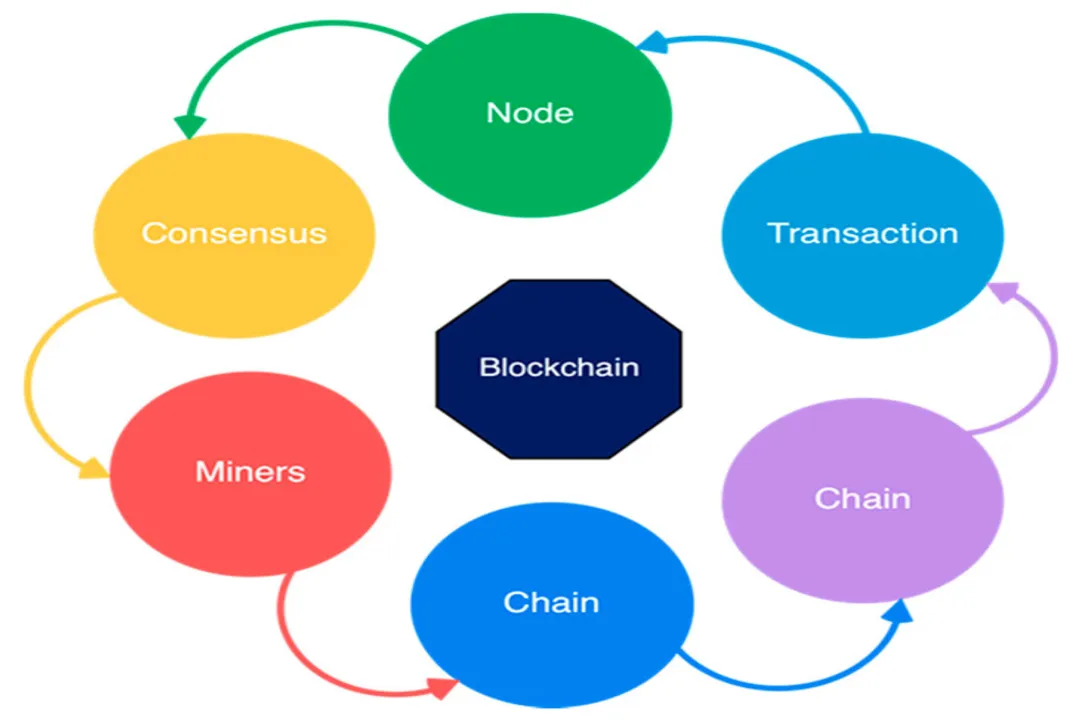
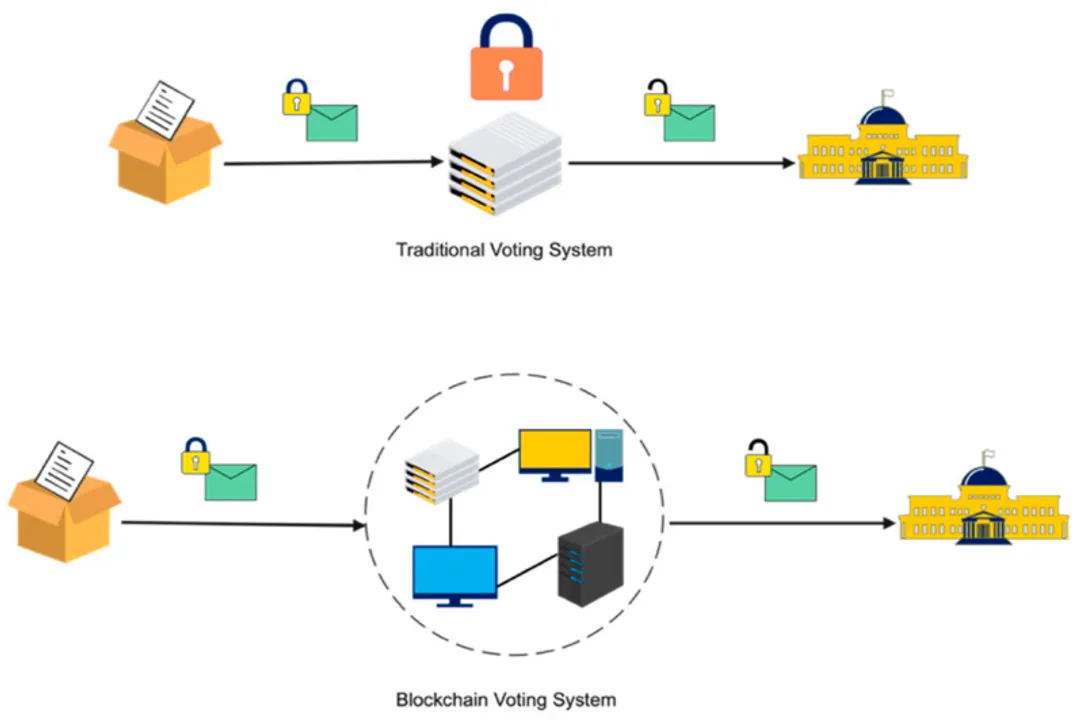
The conversation around e-voting roles is evolving with technologies like blockchain, which fundamentally challenge the traditional centralized nature of election administration. [8] In a traditional electronic system, risk tends to concentrate at the central level (the EMB or vendor) when paper trails are absent. [5] Blockchain technology seeks to diffuse this risk by creating a decentralized consensus role. [8]
In a fully realized blockchain voting system, the need for a single trusted Central Vote Server role diminishes, replaced by multiple Distributed Nodes that validate and store the encrypted vote data. [8] The role of the Miner (or validator) becomes performing the consensus algorithm to ensure immutability of the recorded ledger. [8] This structure aims to make large-scale manipulation theoretically impossible unless a majority of nodes collude (a "51% attack"). [8]
However, this shift introduces new challenges and specialized roles. The complexity of cryptography (like blind signatures or homomorphic encryption) needed to maintain anonymity while ensuring eligibility makes the system obscure to non-experts, thus shifting the trust requirement from an operational one to a cryptographic one. [5][8] Furthermore, while blockchain excels in data integrity, its inherent scalability limits—such as slow transaction speed in public chains—mean it is not yet proven for the high volume of a national election, keeping the immature technology role a major barrier. [8]
For any e-voting system, the essential roles boil down to ensuring the process is Eligible, Unrepeatable, Private, Fair, Sound, and Complete. [8] Whether managed by a central EMB, overseen by state testing laboratories, or secured by cryptographic consensus across decentralized nodes, the roles within the system are constantly balancing the desire for technological speed and convenience against the democratic imperative for transparency and auditable results. [5][7] The pursuit of a trusted system is not a matter of choosing one technology, but ensuring the defined roles—human and machine—are executed with transparency across the entire socio-political, operational, and technical foundations of the election. [5]
The reality is that the system is only as good as the public believes it to be, which puts an enormous weight on the communication role of election officials to explain why a chosen technology is trustworthy, whether it relies on a paper artifact or mathematical proof. [5] Even systems with sound technical foundations can fail if social acceptance is not won over time through gradual implementation and education. [5] Ultimately, the roles within e-voting are a dynamic set of checks and balances, demanding continuous expertise that must be built and retained by the government itself, lest it become too dependent on the very vendors tasked with building the solution. [5] This need for constant local competency building—ensuring local IT staff can troubleshoot and own the system—is a critical, actionable consideration for any jurisdiction moving past initial vendor contracts. [5] It is not enough to simply buy a system; the role of maintenance and ownership must be vested locally for long-term sustainability [5].Electronic voting, or e-voting, encompasses any process that uses electronic means to assist in or handle the casting and counting of ballots. [3] The goal behind adopting this technology often centers on enhancing election efficiency, reducing costs, speeding up result tabulation, and improving accessibility for various populations, such as overseas citizens or those with mobility impairments. [4][5] However, because this technology touches the fundamental act of casting and counting votes, its implementation shifts responsibilities and creates distinct functional and human roles that are essential to maintaining integrity and public confidence. [5][7]
# Functional Components
Within any e-voting system, various functional roles must be performed, whether by dedicated hardware, software, or integrated processes. These functions span the entire voting lifecycle, from a voter making a choice to the final tally being published. [5]
One primary functional role is Vote Input and Marking. This is how the voter interacts with the system. This can range from filling in an oval on a paper ballot that is then scanned, to using a dedicated Ballot Marking Device (BMD). [2] BMDs, often required to provide accessible interfaces like audio, large text, or sip-and-puff devices, play the specific role of translating a voter's intent into a machine-readable format on a physical ballot. [2][3] In systems without paper ballots, such as older Direct Recording Electronic (DRE) systems, this role involves recording the selection directly into computer memory via a touchscreen or buttons. [2]
The second critical function is Vote Recording and Storage. This role determines where the official choice resides. In paper-based electronic systems, the human-readable paper ballot serves as the primary record, and the electronic record is secondary or used only for initial tabulation. [2][5] Conversely, DRE systems primarily record the vote in memory components, which necessitates an audit mechanism like a Voter Verified Paper Audit Trail (VVPAT) to create an independent physical record for verification, a consensus point among security experts. [2][3] Hybrid systems combine these roles, allowing a voter to mark an electronic ballot which is then printed, scanned, and tabulated. [2]
A third major role is Vote Tabulation and Consolidation. This is the role of counting the votes. Some systems, like Precinct Count Optical Scanning (PCOS), execute this at the polling place. Others use a Central Count System where precinct ballots are collected and counted centrally using high-speed scanners. [2][5] In systems using internet voting (i-voting), this function is handled by a Central Vote Server that tallies votes after the remote casting period ends. [7] Even the simple aggregation of results from various tally sheets or machines, often performed using spreadsheets, carries the functional role of final summation, though this step has historically been a source of error if not strictly controlled. [3]
Finally, the system must fulfill the role of Verification and Auditing. This is perhaps the most debated functional role, as systems lacking a paper record can only be verified indirectly through certification and security protocols. [5] Systems with paper trails allow for manual recount verification, where the paper record is the official ballot of record. [2][5] End-to-end verifiable systems aim to provide cryptographic proof that the vote was recorded as cast and tallied as recorded, independent of the underlying software. [3]
# Human Oversight Roles
The proper functioning of these technical roles relies heavily on the human roles involved in the system's lifecycle, from initial development through deployment and auditing. The inherent secrecy required for voting—the separation of voter identity from the ballot—makes the system fundamentally different from standard information technology, placing high importance on the roles responsible for security and oversight. [5][7]
The Electoral Management Body (EMB) or state/local election officials hold the paramount role of ultimate responsibility and ownership. [5] They must define the goals for using e-voting, manage procurement, and ensure the chosen solution fits the local context. [5] In the US, for instance, State Secretaries of State or State Boards of Elections act as the final approving authority for system use within their jurisdictions. [6][9] This role is crucial for retaining oversight and avoiding dependence on the vendors who build the technology. [5]
Vendors and Developers serve the role of system creators. They design, build, and often maintain the proprietary software and hardware. [5] Due to reliance on vendor competence and proprietary code, security experts often argue that the EMB must have access to source code to fulfill its oversight role effectively. [3][5] An interesting tension exists here: vendors are typically reluctant to provide source code access for security or commercial reasons, yet advocacy groups argue that publishing the code allows for broader scrutiny necessary for trust. [5]
Testing Laboratories and Certification Agents fill the vital quality assurance role. In the US, this is formalized by the Election Assistance Commission (EAC), which oversees accredited Voting System Test Laboratories (VSTLs). [6] These labs test systems against the Voluntary Voting System Guidelines (VVSG) to verify functionality, accessibility, and security. [6] State-level bodies, like election commissions or secretaries of state, often use these reports to issue their own certification or approval, creating a layered role of verification. [6][9] For example, in New York, the State Board of Elections tests the system based on EAC guidelines, while in many states, testing must be done by a federally accredited laboratory. [1][6]
Election Administrators and Poll Workers execute the system on Election Day. Their role is operational and procedural, requiring rigorous adherence to established steps—from checking in voters using Electronic Poll Books to verifying zero tapes at poll opening and securing materials post-closing. [1][9] The successful introduction of e-voting often requires significant capacity building and training for these roles, as the responsibility shifts from many localized poll workers to a centralized system managed by fewer, highly trained staff. [5]
Auditors and Observers play the indispensable role of independent verification. This can involve conducting mandated post-election audits, such as the partial manual counts required in some US states, or observing the testing and deployment phases. [5][9] In jurisdictions using paper records like VVPATs, auditors verify the electronic count against the physical evidence. [2][5] When systems are paperless, the audit role becomes one of confirming that the process followed prescribed, certified security procedures, which is inherently more difficult to communicate to the public. [5]
# The Voter's Evolving Role
The voter's role has transformed from simply marking a paper ballot to actively verifying an electronic process. While e-voting offers increased convenience, this convenience comes with the implied responsibility for voter verification.
The voter is expected to confirm that the electronic selections match their intent, often by reviewing a printed VVPAT slip before depositing it. [2][5] In internet voting, this verification role is more abstract, often relying on a Confirmation Code to check that the vote was received unaltered by the server, rather than viewing a physical representation of their choices. [3][5]
An important, though often overlooked, element is the Digital Literacy role required of the modern voter. While e-voting aims to bridge the digital divide for those who are remote or have disabilities, the introduction of complex systems like Ballot Marking Devices or internet voting implicitly demands a baseline level of technical familiarity. [4] If voters do not understand the technology, their ability to perform their verification role—and thus their trust in the outcome—can be compromised. [5] In environments where e-voting systems are only understood by a small cadre of experts, the public trust layer of the E-Voting Pyramid of Trust is severely weakened, regardless of technical soundness. [5] The failure to invest in civic and voter education as a core function of the implementation is a common oversight that stalls social acceptance. [5]
# Regulator Roles in Certification
Across jurisdictions, the role of the regulator is defined by what level of federal standard compliance they mandate. While the EAC's Voluntary Voting System Guidelines (VVSG) provide a baseline for federal certification, state laws dictate the mandatory role of this baseline. [6]
A comparison of state approaches reveals distinct regulatory roles. In some states, like Alaska or Mississippi, the role is to ensure the system is legal and then approve it based on baseline HAVA requirements, without explicitly mandating testing to federal standards by an accredited lab. [6] In contrast, states like Georgia, Kentucky, and Massachusetts establish a more rigorous gatekeeper role, requiring systems to be certified by an EAC-accredited laboratory before the state process even begins, demonstrating a commitment to external validation. [6]
This difference in regulatory posture highlights a key management decision: how much technical burden to delegate to federal testing bodies versus how much to assume internally. Where state bodies appoint technical experts—like Arizona appointing a committee with engineering and bar members—they are assuming a more active, internal technical review role. [6] In contrast, states that rely primarily on federal certification numbers are positioning their certification role as largely administrative compliance checking. [6]
# Emerging Roles (Blockchain)
The conversation around e-voting roles is evolving with technologies like blockchain, which fundamentally challenge the traditional centralized nature of election administration. [8] In a traditional electronic system, risk tends to concentrate at the central level (the EMB or vendor) when paper trails are absent. [5] Blockchain technology seeks to diffuse this risk by creating a decentralized consensus role. [8]
In a fully realized blockchain voting system, the need for a single trusted Central Vote Server role diminishes, replaced by multiple Distributed Nodes that validate and store the encrypted vote data. [8] The role of the Miner (or validator) becomes performing the consensus algorithm to ensure immutability of the recorded ledger. [8] This structure aims to make large-scale manipulation theoretically impossible unless a majority of nodes collude (a "51% attack"). [8]
However, this shift introduces new challenges and specialized roles. The complexity of cryptography (like blind signatures or homomorphic encryption) needed to maintain anonymity while ensuring eligibility makes the system obscure to non-experts, thus shifting the trust requirement from an operational one to a cryptographic one. [5][8] Furthermore, while blockchain excels in data integrity, its inherent scalability limits—such as slow transaction speed in public chains—mean it is not yet proven for the high volume of a national election, keeping the immature technology role a major barrier. [8]
For any e-voting system, the essential roles boil down to ensuring the process is Eligible, Unrepeatable, Private, Fair, Sound, and Complete. [8] Whether managed by a central EMB, overseen by state testing laboratories, or secured by cryptographic consensus across decentralized nodes, the roles within the system are constantly balancing the desire for technological speed and convenience against the democratic imperative for transparency and auditable results. [5][7] The pursuit of a trusted system is not a matter of choosing one technology, but ensuring the defined roles—human and machine—are executed with transparency across the entire socio-political, operational, and technical foundations of the election. [5]
The reality is that the system is only as good as the public believes it to be, which puts an enormous weight on the communication role of election officials to explain why a chosen technology is trustworthy, whether it relies on a paper artifact or mathematical proof. [5] Even systems with sound technical foundations can fail if social acceptance is not won over time through gradual implementation and education. [5] Ultimately, the roles within e-voting are a dynamic set of checks and balances, demanding continuous expertise that must be built and retained by the government itself, lest it become too dependent on the very vendors tasked with building the solution. [5] This need for constant local competency building—ensuring local IT staff can troubleshoot and own the system—is a critical, actionable consideration for any jurisdiction moving past initial vendor contracts. [5] It is not enough to simply buy a system; the role of maintenance and ownership must be vested locally for long-term sustainability. [5]
Related Questions
#Citations
Electronic voting - Wikipedia
What is e-voting? Who's using it and is it safe? | World Economic ...
Voting Equipment - Verified Voting
Internet Voting: Past, Present and Future | IFES
[PDF] Introducing Electronic Voting: - EODS
[PDF] Overview of Voting Systems Testing and Certification in the United ...
Voting Technology | New York State Board of Elections
The Evolution of Voting Technology - American Bar Association
Blockchain for Electronic Voting System—Review and Open ...
Electronic Voting System Procedures - the Texas Secretary of State

